Friday, February 22, 2013
Hidden security threats on enterprise networks
View the Original article
Real world social engineering challenge at HITBSECCONF2013
View the Original article
Mandiant APT1 report used as a lure in phishing campaigns
View the Original article
Zendesk hack endangers Tumblr, Twitter and Pinterest users
View the Original article
OAuth flaw allowed researcher full access to any Facebook account
View the Original article
Mobile phishing geared towards online banking users
View the Original article
Thursday, February 21, 2013
Duo Security launches secure mobile ID
View the Original article
F5 Networks releases hybrid cloud solution for mobile application management
View the Original article
Anonymous hacks U.S. State Department and investment firm, leaks data
View the Original article
The sophistication of risky apps, mobile misbehavior and spyware
View the Original article
Security pros should listen with their heads, not their hearts
View the Original article
Chinese Army unit is behind cyber espionage campaigns, researchers claim
View the Original article
Qualys CEO to address security in a hyperconnected world at RSA Conference 2013
View the Original article
Alert Logic releases new log manager
View the Original article
SmishGuru simulated attack service launches
View the Original article
Tips to overcome PHI security obstacles
View the Original article
How CSOs are enabling secure BYOD
View the Original article
Apple confirms being hit in recent watering hole attack
View the Original article
12.6 million identity fraud victims identified in the U.S.
View the Original article
Oracle, Apple release critical updates for Java
View the Original article
$400 million risk lurking inside global enterprises
View the Original article
Twitter entreats users to use better passwords
View the Original article
Adobe patches Acrobat and Reader, Mozilla debuts Firefox built-in PDF viewer
View the Original article
Check Point introduces high-performance data center security appliance
View the Original article
Cenzic Enterprise integrates with F5 BIG-IP ASM
View the Original article
FireMon expands situational awareness with Security Manager 7.0
View the Original article
Security is top reason why IT adopts single sign-on
View the Original article
Google account hijacking dramatically reduced
View the Original article
25% of DDoS attacks in 2013 will be application-based
View the Original article
Twitter calls for smarter password habits following Jeep, Burger King hacks
View the Original article
China's Defense Ministry calls accusations of state-sponsored hacking groundless
View the Original article
China biggest, but not the only country engaged in cyberespionage
View the Original article
Chinese Government's Link to Cyber Espionage Clearer Than Ever
View the Original article
Many companies likely affected by iOS developer forum compromise
View the Original article
Identity fraud in US reaches highest level in three years
View the Original article
The cyber war is real -- and our defenses are weak
I used to think "cyber war" was the most overhyped security buzzphrase of all time. And it was -- until Stuxnet and APTs (advanced persistent threats) arrived. Now, as Bob Violino detailed in his recent InfoWorld article, all-out cyber war has begun.
View the Original article
Ubuntu Touch Preview coming to Nexus tablets this week
After desktops and phones, Ubuntu is now bringing its Linux distribution to tablets. Coming Thursday, preview images for Google's Nexus tablets will be released, so we can all get a good long look at what Canonical is cooking up. They've published a YouTube video which details all that Ubuntu has to offer for tablets, and to be honest, it's looking quite good.
View the Original article
Higgs Boson calculations add up to new Armageddon scenario
Anyone who thinks the end is nigh with a giant asteroid colliding into Earth may have a new apocalypse scenario to worry about.
It all boils down to the Higgs Boson particle, aka the "God particle."
View the Original article
A look at Mandiant and their allegations on China hacking
A private technology security firm on Tuesday described in extraordinary detail efforts it blamed on a Chinese military unit to hack into 141 businesses, mostly inside the U.S., and steal commercial secrets. China denies the claim. Here's a look at the company, Mandiant, and why its report is significant.
What is Mandiant?
View the Original article
Microsoft's Windows Blue may have just hit milestone 1
The Windows team at Microsoft just completed the first milestone build (M1) of Windows Blue, the first full-fledged update to Windows 8, according to a couple of sources of mine.
windowsbluem1
One of my contacts said that M1 marks the half-way point in the Windows Blue development schedule. The last and final milestone build of Windows Blue will be M2, said this contact, who requested anonymity.
View the Original article
How to Force an Android Device to Find a System Update
Whenever Google releases a new version of Android for its Nexus devices, it doesn’t roll out to everyone at once. It may take several days before your device receives the update, but you don’t have to wait.
Note that this only works if an OTA (over-the-air) update is actually available – for example, if you’ve got a Nexus 4 running Android 4.2.1 and you haven’t yet received a notification to update to Android 4.2.2. This won’t help if you’re using an Android device that isn’t receiving updates.
View the Original article
How Anonymous accidentally helped expose two Chinese hackers
How did security firm Mandiant put names to two previously unknown Chinese hackers who, it says, steal American corporate secrets for the Chinese government? With a little inadvertent help from Anonymous.
View the Original article
Google Glass' user interface revealed
This is amazing. Not only has Google just opened up the pre-order program for Google Glass to 'creative individuals', it has also unveiled what the user interface looks like and how it works. It's... Nothing short of amazing. I'm throwing money, credit cards, my car keys, my house keys, my Surface RT, my cats, everything at my screen. I want this so bad.
View the Original article
Twitter's Response To The Burger King Hacking: Do A Better Job At Protecting Your Password
In response to the hacking of Burger King and Jeep's Twitter accounts this week, Twitter put up a new blog post encouraging people to protect their passwords.
Here are Twitter's tips:
View the Original article
BlackBerry squashes W-TIFF-F bug that's ripe for malware squirters
BlackBerry has patched a security vulnerability that allowed hackers to run malicious code on systems running its BlackBerry Enterprise Server (BES) software.
The bug, rated as "high severity", is triggered by specially crafted TIFF image files that travel into BES as users visit webpages, receive emails and exchange instant message conversations.
View the Original article
Wednesday, February 20, 2013
China steps up defence on hacking allegations
Chinese state media stepped up the war of words on Thursday over allegations of sophisticated cyberattacks on US firms, branding the accusations a "commercial stunt" and accusing Washington of ulterior motives.
American Internet security firm Mandiant earlier this week said that a Chinese military cyberspy unit is targeting US and other foreign firms and organisations with hacking attacks.
View the Original article
Apple releases 'malware removal tool' following computer hack
Apple will release a malware removal tool after a number of Mac systems were infected by computer hackers who targeted Facebook last week.
Unknown hackers infected the computers of some Apple workers when they visited a website for software developers that had been infected with malicious software.
The malware had been designed to attack Mac computers, the Telegraph reports. The same software, which infected Macs by exploiting a flaw in a version of Oracle Corp's Java software used as a plug-in on Web browsers, was used to launch the attacks against Facebook.
View the Original article
Forum site gives more details on Apple and Facebook hacks
The popular forum site that hackers used to access employee computers at Apple and Facebook gave more details today on how the cyberattack happened.
The site's owner Ian Sefferman confirmed previous reports that hackers injected JavaScript into his site, iPhonedevsdk, and were then able to use a previously unknown exploit to access certain user's computers. He also said that the cyberattack most likely ended on January 30, 2013.
View the Original article
MTV, BET 'Hack' Stunt Backfires
The popular networks unsuccessfully tried to 'Catfish' their respective followers. We have details on how they failed miserably after the jump.
In an apparent move to gain Twitter followers, the sister networks pretended hackers took over their accounts.
View the Original article
First space tourist plans to make trip to Mars in 2018
Earth's first space tourist won't be outdone by a few fancy NASA rovers with their cutesy names, sky cranes and whatnot. So like the saying goes, if you can't beat 'em, make the unprecedented 500-day round-trip journey to Mars to join 'em.
That's the insanely ambitious plan that Dennis Tito, who was the first private space traveler a little less than 12 years ago will announce in more detail next week.
View the Original article
Making sense of the PS4 game lineup
So the world didn't exactly get what it wanted out of Sony's PlayStation 4 debut tonight. There was no sight of the actual console itself and details about its specific release date and price were also nowhere to be seen.
Sony's team-up with Gaikai is sure to net some interesting ideas and implementations with cloud streaming, the sharing of game screens, remote play and other concoctions, but it was the games themselves that made the biggest impact.
View the Original article
Adobe's emergency patch for Reader and Acrobat is here
Adobe has released the emergency update for Reader and Acrobat that it promised late last week.
The company decided to get a move on to deal with a newly-reported vulnerability that was actively being exploited, at least on Windows and the Mac.
The timeline has been pretty swift:
2012-02-12: Bug reported in a blog post by FireEye. Details scant.
2013-02-13: Adobe publishes a security bulletin, including a workaround for Windows users.
2013-02-17: (Weekend) Adobe announces patch "next week."
2013-02-20: Patch is released.
View the Original article
McAfee finds sophisticated attacks targeting other 'critical sectors' of the economy
Financial services has been a favorite target for sophisticated attacks in the last few years, but cyber criminals are moving on to other "critical sectors of the economy," according to McAfee.
In the security giant's fourth quarter threats report, researchers highlighted some of the new schemes being used in this regard and other high-profile attacks, including advanced persistent threats (APTs) such as Operation High Roller and Project Blitzkrieg.
View the Original article
Identity fraud in U.S. is on the rise, report
While cyberattacks and hacking seem to be constantly making headlines these days, identity fraud is also on the rise.
A new report by Javelin Strategy and Research shows that identity fraud has increased for the last three years in a row -- affecting more than 5 percent of U.S. adults. In 2012, 12.6 million people were identity victims.
View the Original article
Mandiant's China Hacking Claims Draw Criticism
Maybe it wasn’t China. Maybe it was, but suppose it wasn’t. That’s the reaction of at least one computer security consultant to yesterday’s blockbuster report from the security firm Mandiant, which accused a unit of China’s People’s Liberation Army of carrying out a series of hacking attacks against companies in the U.S., Canada, the U.K. and elsewhere over a series of years.
Jeffrey Carr, CEO of Taia Global, writes today in a blog post that he thinks Mandiant’s report is full of holes.
View the Original article
Tuesday, February 19, 2013
Washington National Guard: Model for Cyber Defense?
The Washington National Guard is leveraging a decade of investment in cyber security at Camp Murray in Lakewood into projects that could protect state and local governments, utilities and private industry from network attacks.
The aim is to bring to the digital world the kind of disaster response the National Guard already lends to fighting wildfires and floods, said Lt. Col. Gent Welsh of the Washington Air National Guard.
“Just as ‘Business X’ needs the National Guard to come in and fill sand bags, ‘Business X’ might need to call the National Guard if it’s overwhelmed on the cyber side,” Welsh said.
The new task plays to a growing strength in the state’s National Guard, which draws on employees from companies including Microsoft and Amazon to provide special expertise in its network warfare units.
I first learned of this initiative when Russ Tweeted about it in June. In an email exchange he described his role in the Washington State Guard (WSG):
"The WSG is an all volunteer force that is a state defense force, with what is typically an emergency management mission. See Title 38 of the Revised Code of Washington (RCW). WSG is also authorized by Federal law, Title 32 of the United States Code.
We most often serve as liaison officers in support of the Emergency Support Function (ESF) 20 (defense support for civilian authorities) function per Federal Emergency Management Agency (FEMA) National Incident Management System (NIMS) / Incident Command System (ICS) guidance during major events (disasters, natural or human caused).
WSG remains a place where extremely experienced soldiers who have exceeded age requirements for active/reserve service can continue to serve as well as folks like me with no prior service who can't get the federal services to consider them for age reasons.
We can be called to active duty but in-state only. I was on active duty with orders for two days in June for a major statewide exercise. When we're called up for such activity we become peer in rank and responsibility to our National Guard counterparts.
I'll also be seeing some active duty time again in the immediate future in support of the initiatives mentioned in the article."
I think this is a great start on a journey towards applying private sector expertise to national digital security problems, but on a local scale. The News Tribune article mentions that the Guard (in all its forms) is working to figure out how it can provide help to besieged companies, from a legal and logistical perspective.
I think this line from the news article summarizes a key theme in this discussion:
"We're not going to wait for the feds to hand us everything," Welsh said.
In our Federal system, we should allow the States (per the 10th Amendment) the freedom to innovate, and thereby invent multiple approaches to fighting digital threats.
View the Original article
Review of Super Scratch Programming Adventure! Posted
 Amazon.com just posted a joint review by myself and my daughter of No Starch's new book Super Scratch Programming Adventure!. From the five star review:
Amazon.com just posted a joint review by myself and my daughter of No Starch's new book Super Scratch Programming Adventure!. From the five star review: I asked my almost-8-year-old to share her thoughts on Super Scratch Programming Adventure! She chose five stars and wrote the following:
"I think it's a very great book. I love the storyline, but my main concern is that I could not find a trace of the Super Scratch folder.
How hard is it to draw the Mona Lisa? I have Scratch version 1.4, and I found it difficult drawing Le Louvre.
On the flip side, I learned a lot. Who knew you could make Scratchy move with 1) arrow keys and 2) a medium sized Script?
I enjoyed watching the Magic Star Web change colors.
Overall, I think it's a very great book, and I highly recommend it to anyone who is interested in programming."
I agree that this is a great book. My daughter wanted to learn how to program a video game, and I thought it would be a lot more difficult. Shortly after starting to read and apply this book, she coded a video game!
I'd like to thank No Starch for sending us a review copy.
View the Original article
Do Devs Care About Java (In)Security?
Is Java 7 currently safe to use?
Last week, Oracle released emergency updates to fix zero-day vulnerabilities in Java 7 and Java 6. But in the case of the Java 7 fix, the new version allows an existing flaw--spotted by security researchers and disclosed to Oracle earlier this year--to be exploited to bypass the Java sandbox. In other words, while fixing some flaws, Oracle opened the door to another one.
In light of that situation, multiple security experts said that businesses should continue to temporarily disable all Java use, whenever possible. "There are still not-yet-addressed, serious security issues that affect the most recent version of Java 7," said Adam Gowdiak, CEO and founder of Poland-based Security Explorations, which initially disclosed the exploited vulnerabilities to Oracle in April. "In that context, disabling Java until proper patches are available seems to be an adequate solution," he said via email.
A month later I read a new article in InformationWeek titled "Oracle's Java Revival," also available as Two Years Later: A Report Card On Oracle's Ownership of Java by Andrew Binstock. The article appeared in the 29 October 2012 issue of InformationWeek, at a time when the security community continued to reel from repeated hammering of Java vulnerabilities.
I expected some mention of Java security woes in the article. About halfway through, with the word "security" not yet in print, I found the following:
In 2011, Oracle did not fare much better. The welcome release of Java 7 was marred by the revelation that it included serious defects that the company knew about.
Ok, maybe there will be some expansion of this idea? Shouldn't a terrible security record be a major factor affecting enterprise use of Java and a reflection on Oracle's handling of Java? Instead I read this:
I'm inclined to agree with James Gosling's revised opinion of Oracle's stewardship, that it's been good for Java...
However, the record is mixed in other areas...
Oracle's ambiguous relationship with the JCP and the OSS communities remain two other weak points.
That's it? Security pros continue to tell enterprise users to disable Java, and the development community is more concerned about features, personalities, and community relations?
I think the Java development community, and especially Oracle, must reevaluate their responsibilities regarding security. Otherwise, they may find themselves coding for a platform that enterprise users will increasingly disable.
View the Original article
Commander's Reading List
 Last month a squadron commander asked me to recommend books for his commander's reading list. After some reflection I offer the following.
Last month a squadron commander asked me to recommend books for his commander's reading list. After some reflection I offer the following. I've divided the list into two sections: technical and nontechnical. My hope for the technical books is to share a little bit of technical insight with the commander's intended audience, while not overwhelming them. The plan for the nontechnical items is to share some perspective on history, policy, and contemporary problems.
The list is in no particular order.
Nontechnical books:
- America the Vulnerable by Joel Brenner
- Cyber War by Richard Clarke and Robert Knake
- Crypto by Steven Levy
- Geekonomics by David Rice
- Security Metrics by Andrew Jaquith
- The Victorian Internet by Tom Standage
- The Cuckoo's Egg by Cliff Stoll
- Tiger Trap by David Wise
Technical books:
- Software Security by Gary McGraw
- The Art of Computer Virus Research and Defense by Peter Szor
- Real Digital Forensics by Keith Jones, Curtis Rose, and Richard Bejtlich
- Incident Response by Kevin Mandia, Matt Pepe, and Chris Prosise
- The Internet and Its Protocols by Adrian Farrell
- The Tao of Network Security Monitoring by Richard Bejtlich
- Hacking Exposed 7 by Joel Scambray, George Kurtz, Stuart McClure, and a ton of contributors
Update: For the more technically-minded reader, I'm adding the following:
Practical Malware Analysis by Michael Sikorski and Andrew Honig.
Note: The above do not necessarily constitute my "best" or "favorite" books. Please see Best Books for blog posts on that subject.
View the Original article
Recommended: The Great Courses "Art of War" Class
For example, did you know that "Sun Tzu" didn't write "The Art of War?" An anonymous author wrote the book in the 4th century BC, based on Sun Tzu's lessons from his time in the 6th century BC.
Also, "The Art of War" isn't even the name of the book! It's actually "Master Sun's Military Method." Furthermore, the use of the term "Master" is significant as it was a term not usually associated with generals.
I especially like two aspects of the course. First, the lecturer, paraphrasing his own words, didn't choose to simply peruse TAOW looking for trite phrases. He equates that approach with telling a stock broker to "buy low, sell high." Instead, Prof Wilson is more concerned with explaining the context for the book and what the words really mean.
Second, the lecturer extends his discussion beyond the history of China's Warring States Period, the era from which TAOW was born. Prof Wilson applies lessons from the book to military history and business situations. He also applies TAOW to modern Chinese cyber espionage, showing he keeps current with contemporary issues.
Consider buying TAOW as a holiday gift for yourself or your friends!
View the Original article
Spectrum of State Responsibility
ACUS published the report in February, but I'm not hearing anyone using the terms described therein. Probably my favorite aspect of the paper is the chart pictured at left. It offers a taxonomy for describing state involvement in digital attacks, ranging from "state-prohibited" to "state-integrated."
I recommend using the chart and ideas in the paper as a starting point the next time you have a debate over digital attribution.
View the Original article
Why Collect Full Content Data?
 I recently received the following via email:
I recently received the following via email: I am writing a SANS Gold paper on a custom full packet capture system using Linux and tcpdump. It is for the GSEC Certification, so my intent is to cover the reasons why to do full packet capture and the basic set up of a system (information that wasn't readily available when setting my system up)...
I am already referencing The Tao of Network Security Monitoring.
These are the questions that I came up with based on questions other peers have asked me...
Here are the questions, followed by my answers. Most of this is covered in my previous books and blog posts, but for the sake of brevity I'll try posting short, stand-alone responses.
- As an information security analyst in today's threat landscape why would I want to do full packet capture in my environment? What value does have?
Full content data or capturing full packets provides the most flexibility and granularity when analyzing network-centric data. Unlike various forms of log data, full content data, if properly collected, is the actual data that was transferred -- not a summarization, or representation, or sample.
- Where should I place a full packet capture system on my network - are ingress/egress points sufficient?
I prioritize collection locations as follows:
- Collect where you can see the true Internet destination IP address for traffic of interest, and where you can see the true internal source IP address for traffic of interest. This may require deploying two traffic access methods with two sensors; so be it.
- Collect where you can see traffic to and from your VPN segment. Remember the previous IP address requirements.
- Collect where you can see traffic to and from business partners or through "third party gateways." You need to acquire the true source IP, but you may not be able to acquire the true destination IP if the business partner prevents collecting behind any NAT or security devices that obscure the true destination IP.
- Collect where your business units exchange traffic. This is more of a concern for larger companies, but you want to see true source and destination IPs (if possible) of internal traffic as they cross business boundaries.
- Consider cloud or hosted vendors who enable collection near Infrastructure-as-a-Service platforms used by your company.
- What advantages are there to creating a custom server with open source tools (such as a server running Linux and capturing with tcpdump) opposed to buying a commercial solution (like Solera or Niksun)?
A custom or "open" platform enables analysts to deploy the sorts of tools they need to accomplish their security mission. Closed platforms require the analyst to rely on the information provided by the vendor.
- Now that I have full packet data, what kind of analysis goals should I have to address advanced threats and subtle attacks?
The goal for any network security monitoring operation is to collect and analyze indicators and warnings to detect and respond to intrusions. Your ultimate role is to detect, respond to, and contain adversaries before they accomplish their mission, which may be to steal, alter, or destroy your data.
- Any other advice for an analyst just getting started with full packet capture systems and analyzing the data?
Rarely start with full content data. Don't dump a ton of traffic into Wireshark and start scrolling around. I recommend working with session data (connection logs) and application-specific logs (HTTP, DNS, etc.) to identify sessions of interest, then examine the content if necessary to validate your suspicions.
I could write a lot more on this topic. Stay tuned.
View the Original article
The Value of Branding and Simplicity to Certifications
In my opinion, the primary reason the CISSP is so successful is that it is easy to understand it, which facilitates marketing it. It is exceptionally easy for a recruiter to search LinkedIn profiles, other databases, or resumes for the term "CISSP." If you encounter a person with the CISSP, you basically know what the person had to do to get the certification.
Before continuing, answer this quick question: what are the following? 1) SSCP, 2) CAP, 3) CSSLP?
Let me guess -- you didn't recognize any of them, just like I did?
Now, let me see if you recognize any of the following? 1) GGSC-0400, 2) GNET, 3) GAWN-C, 4) GBLC, 5) GCIM?
I believe you didn't recognize any of those either.
How about? 1) GISP, 2) GLEG, 3) GCIH, 4) GAWN?
I'm guessing some of you might recognize GCIH as the SANS "GIAC Certified Incident Handler," which actually doesn't have much to do with "incident handling." That's a topic for another day, but it does show GCIH benefits from decent branding.
You've probably figured out that the last two lists of acronyms were SANS certifications. The first list was a selection of a few of the retired SANS certifications. There's 26 of those.
The second list was a selection from the list of 24 active SANS certifications.
What about the first list, starting with "SSCP?" Those are other certifications offered by ISC2. They're utterly forgettable. Had I not visited the ISC2 Web site, I would never have known they existed.
Now, one could argue that the brand "SANS" is as recognizable, or even more recognizable, than the brand "CISSP."
The problem is that a person's resume could list "SANS" as a course he or she attended, without noting if a certain achievement (i.e., certification) was achieved. "SANS" is also a poor search term because the diversity of the SANS ecosystem means you could be dealing with a legal person, or a reverse engineer, or a UNIX system administrator.
What is the answer for SANS, if the CISSP will likely continue to out-market it? I recommend adopting the model used by Cisco. If you hear a person has a CCIE, that means something -- you immediately think of deep knowledge, several levels of work, and grueling hands-on testing over two days in a controlled environment.
The genius of Cisco's approach is that they have "tracks" for the CCIE, e.g. Data Center, Routing and Switching, etc. Those aren't the brands though; that stays with CCIE.
The Cisco approach isn't perfect, because you can't simply search resumes for "CCIE" intending to get a CCIE in security. You might find a CCIE in routing and switching, or wireless. However, if one finds a CCIE, you get a sense of the level of seniority and ability to operate in a stressful environment (at least as far as a test can simulate).
SANS has tried something like the CCIE with their "GIAC Security Expert (GSE)." The GSE is similar to the CCIE in many respects, including horribly tough hands-on labs, but unfortunately hardly anyone knows about it. It is really difficult to reach that level in SANS certification. However, because only 63 people hold it, there's no real market for them.
By the way, I smell a branding failure when SANS certifications like GSE, GCIH, and so on all have a "G," which references another acronym -- "GIAC," for "Global Information Assurance Certification." That doesn't even include the term "SANS," which is the stronger brand. GIAC originally meant "Global Incident Analysis Center," but that's another story.
In brief, I think SANS could increase the branding value of their certifications if they retired the existing acronyms and names, incorporated "SANS" into a new naming scheme, and concentrated on a "level" approach seen with Cisco. Focus on Entry-Level, Associate, Professional, and Expert as Cisco does, and develop programs to accelerate the adoption of the Expert level among its constituency as Cisco did with CCIEs.
Rebranding would cause lots of SANS folk plenty of heartache, but I think integrating "SANS" into the new level-oriented structure would more than compensate for the initial transition costs. Ultimately the system would be stronger for everyone.
What do you think?
View the Original article
Five No Starch Books for Kids, Reviewed by Kids
 No Starch was kind enough to send me five books for kids, which I asked my 6- and 8-year-old daughters to read. (I didn't need to "ask," really -- like my wife and I, our daughters think reading is something you have to be told "not" to do, e.g., "put the book down; we don't read at the dinner table.")
No Starch was kind enough to send me five books for kids, which I asked my 6- and 8-year-old daughters to read. (I didn't need to "ask," really -- like my wife and I, our daughters think reading is something you have to be told "not" to do, e.g., "put the book down; we don't read at the dinner table.") I did have to encourage my daughters to review the books. Although the older one writes book reports for school, she's not accustomed to writing reviews for books sent by publishers.
The five books, with links to the Amazon.com reviews, are:
- Python for Kids
- The Unofficial LEGO Technic Builder's Guide
- The Unofficial LEGO Builder's Guide
- The LEGO Adventure Book, Vol. 1: Cars, Castles, Dinosaurs & More!
- Wonderful Life with the Elements: The Periodic Table Personified
I agree with my daughters: all five of these books are excellent. However, for readers of this blog who have kids, I would most strongly recommend the Python book. I would start with the book we previously reviewed, Super Scratch Programming Adventure!, and then see what your kid can do with Python.
Kudos to No Starch for publishing high quality books that teach kids skills they can use in the work place (programming), or for fun!
View the Original article
2012: The Year I Changed What I Read
 If you've been reading this blog for a while, you probably know that reading and reviewing technical books has been a key aspect since the blog's beginning in January 2003. In fact, my first blog post announced a review of a book on Border Gateway Protocol (BGP).
If you've been reading this blog for a while, you probably know that reading and reviewing technical books has been a key aspect since the blog's beginning in January 2003. In fact, my first blog post announced a review of a book on Border Gateway Protocol (BGP). Looking at my previous reviews, it's clear that my interest in reading and reviewing technical books expired in the summer of 2011. Since then, the only technical book I wanted to read and review was Michael W. Lucas' excellent SSH Mastery. MWL is such a great author that I read just about anything he writes, and I was interested in his first self-published technical work.
So what happened? Becoming CSO at Mandiant in April 2011 contributed to my changing interests. Since that time I've spoken to almost a hundred reporters and industry analysts, and hundreds of customers and prospects, answering their questions about digital threats and how best to live in a world of constant compromise. (I listed some of the results of talking to the reporters on my press page.)
For me, the most interesting questions involved history, political science, and public policy. Probably not be accident, these are the three subjects in which I have degrees.
Accordingly, I bought and read books to add the historical, political, and policy content I needed to balance my technical understanding of the threat landscape. I also read a few books based purely on personal interest, without a work connection.
I thought you might want to know what these books were, despite my lack of interest in reviewing them at Amazon.com.
The books on Chinese topics included:
- Chinese Intelligence Operations
- China's Techno-Warriors: National Security and Strategic Competition from the Nuclear to the Information Age
- 21st Century Chinese Cyberwarfare
- Chinese Cyber Nationalism: Evolution, Characteristics, and Implications
- China's Rising Global Profile: The Great Power Tradition
Of these five, the first was probably the most interesting. The way Chinese intelligence agencies work today appears very much the same way that the author described them almost twenty years ago.
I read three books on intelligence and Russia:
- For the President's Eyes Only: Secret Intelligence and the American Presidency from Washington to Bush
- Recasting the Red Star
- Cyber Silhouettes: Shadows Over Information Operations
Of these three, the first was exceptional. It combined a history of the US with a history of intelligence through the end of Bush 41's term.
Finally, I read two other books; one related to security, and one completely unrelated:
The first was Bruce Schneier's latest, which I found largely interesting. I recommend reading it, because it may convince you that all the technical safeguards our industry pursues contribute probably less than 10% of the risk mitigation we need in the real world.
The second was another biography of my favorite historical figure, US Grant.
I'm trying to finish Tim Thomas' latest book, Three Faces of the Cyber Dragon, by the end of tomorrow, as well.
In my last post of 2012 I'll announce my Best Book Bejtlich Read in 2012 winner.
View the Original article
Best Book Bejtlich Read in 2012
 It's time to name the winner of the Best Book Bejtlich Read award for 2012!
It's time to name the winner of the Best Book Bejtlich Read award for 2012! I started seriously reading and reviewing digital security books in 2000. This is the 7th time I've formally announced a winner; see my bestbook label for previous winners.
I posted yesterday that 2012 was the year I changed what I read. For example, in 2011 I read and reviewed 22 technical books. In 2012, which a change in my interests, I only read and reviewed one technical book. Thankfully, it was a five star book, which means it is my BBBR 2012 winner!
 As you might have figured out yesterday, this year's winner is SSH Mastery by Michael W Lucas. Feel free to read my Amazon.com review for details. Note that I bought a Kindle version from Amazon.com, and later MWL mailed me a print copy.
As you might have figured out yesterday, this year's winner is SSH Mastery by Michael W Lucas. Feel free to read my Amazon.com review for details. Note that I bought a Kindle version from Amazon.com, and later MWL mailed me a print copy.
Besides the excellent style and content, one of the reasons I read the book was to experience MWL's first release of a self-published technical book. I think it was a successful endeavor, although I'm not prepared to try that route myself anytime soon.
If I were to name my favorite non-technical book I read in 2012, it would be For the President's Eyes Only: Secret Intelligence and the American Presidency from Washington to Bush by Christopher Andrew. I enjoyed learning more about American history through the eyes of the intel world, but I was shocked by how poorly most presidents understood and (mis)used intelligence.
I'm probably done reading and reviewing technical books, so I consider this to be the final BBBR post. I have over 100 possible (mainly nontechnical) books to read on my Kindle now (in Sample form), but I doubt I will review them when done.
Good luck reading in 2013!
View the Original article
Security Onion + (ELSA or Snorby) + CapMe = Awesome
Monday Doug Burks released Security Onion 12.04. Please read Doug's post to learn how great this new 64 bit release is. I wanted to highlight a few features of the new release which takes Network Security Monitoring with open source tools to a new level for security analysts.
12.04 ships with Martin Holste's Enterprise Log and Search Archive (ELSA) working out of the box. Thanks to close integration with the latest version of Bro, analysts have Web-based, indexed access to Bro logs.
If that weren't enough, 12.04 also ships with a late addition -- Paul Halliday's CapMe. What this means is that you can now access full TCP transcripts from any alert in Dustin Webber's Snorby or Martin's ELSA.
You might not appreciate that right away, but it's a step in the right direction. Thus far, Bamm Visscher's Sguil has been the de facto open source NSM reference tool, allowing analysts to easily pivot from alert or session data to full pcap data. Now, with ELSA + CapMe, analysts can pivot from any log entry of TCP traffic with timestamps, IP addresses, protocols, and ports to a Web-based rendering of a transcript.
This is key: this transcript was not saved because of the log or alert. It was saved simply because the traffic was seen on the wire and netsniff-ng recorded it. This is one way to better handle threats who know how to evade signature-based systems.
This new workflow/feature is what I chose to depict in the screen shot at left. The upper window shows ELSA with a query for a BRO_HTTP log for www.testmyids.com. I then invoke CapMe and generate the transcript in the window at bottom. You can do the same from alert data in Snorby.
This is only the first step in giving analysts more data via open source software. Great work Security Onion team!
View the Original article
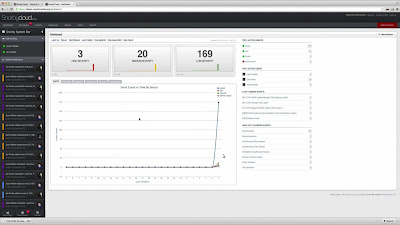
Welcome to Network Security Monitoring in the Cloud
I just watched an incredible technical video. If you have about 10 minutes to spare, and want to be amazed, take a look at Snorby Cloud.
I think the video and Web site does an excellent job explaining this new offering, but let me provide a little background.
Many of the readers of this blog are security pros. You're out there trying to defend your organization, not necessarily design, build, and run infrastructure. You still need tools and workflows that accelerate your incident detection and response process though. So, you work as a security admin, system admin, storage admin, database admin... you get the picture. You manage to keep up, but you probably wish you could focus on finding bad guys, as quickly as possible, without taking care of all the *stuff* that you need to do your job.
While many of you are security experts, some are just beginning your journeys. The responsibilities of being an admin of four or more different shades is overwhelming. Furthermore, you don't have the experience, or budget, or support to get the security data and escalation paths needed to defend your network. How can you improve your skills when you're constantly overwhelmed?
Both kinds of users -- senior and junior alike -- are going to find something intriguing about Snorby Cloud. Maybe you've heard of Snorby before, as a Web-based interface to Network Security Monitoring data. Doug Burks packages it with Security Onion (SO), and you can try it via live CD or .iso in a VM. It looks great on my iPad! There's even a mobile version on iTunes.
Snorby Cloud would be cool if it just put the Snorby Web application in the cloud, and managed the administrative side of security infrastructure for you. For example, you'd log into the cloud interface and be greeted by the graphs you remember from traditional Snorby.
However, you have to think of this as a new, better version of Snorby, collecting far more useful data, and making it rapidly available to the analyst. For example, the following shows SMTP logs available in the interface:
You can just as easily access host-based logs for the same victim computer:
As you investigate the incident, you can see who else on your team is working and what they did. You can also chat with them in real time.
I could say a lot more about this new tool, but I think watching the video will convey some of what it can do. My next step is to get the agents running on a test network so I can drive the console myself and become more familiar with it.
Snorby Cloud is a product from Packet Stash. Follow them at @packetstash for updates.
Disclaimer: I'm friends with this team; I hired two of the co-founders into GE-CIRT, and later worked with all three co-founders at Mandiant.
View the Original article